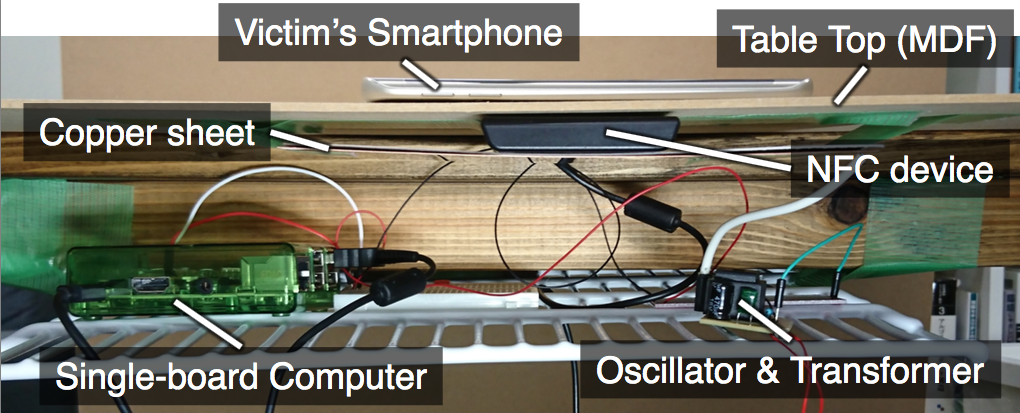
We present a novel attack named “Tap ‘n Ghost“, which aims to attack the touchscreens of NFC-enabled mobile devices such as smartphones. Tap ‘n Ghost consists of two striking attack techniques — “Tag-based Adaptive Ploy (TAP)” and “Ghost Touch Generator.” First, using a NFC card emulator embedded in a common object such as table, a TAP system performs tailored attacks on the victim’s smartphone by employing device fingerprinting; e.g., popping up a customized dialogue box asking whether or not to connect to an attacker’s Bluetooth mouse. Further, Ghost Touch Generator forces the victim to connect to the mouse even if she or he aimed to cancel the dialogue by touching the “cancel” button; i.e., it alters the selection of a button on a screen. After the connection is established, the attacker can remotely take control of the smartphone, with the knowledge about the layout of the screen derived from the device fingerprinting. To evaluate the reality of the attack, we perform an online survey with 300 respondents and a user study involving 16 participants. The results demonstrate that the attack is realistic. We additionally discuss the possible countermeasures against the threats posed by Tap ‘n Ghost.
Preprint version
Seita Maruyama, Satohiro Wakabayashi, Tatsuya Mori “Trojan of Things: Embedding Malicious NFC Tags into Common Objects,” arXiv:1702.07124 [cs.CR] https://arxiv.org/abs/1702.07124
Paper
S. Maruyama, S. Wakabayashi, and T. Mori, “Tap ‘n Ghost: A Compilation of Novel Attack Techniques against Smartphone Touchscreens,” Proceedings of the 40th IEEE Symposium on Security and Privacy (S&P 2019), pp. 628-645, May 2019 (acceptance rate = 12.5%=84/673) [PDF][slide][YouTube]
People
- Seita Maruyama
- Satohiro Wakabayashi
- Tatsuya Mori
Talk
Short Video
Photos
Media
- 2019/6/1 New attack creates ghost taps on modern Android smartphones (ZDNet)
- 2019/6/3 Tap ‘n Ghost Attack Creatively Targets Android Devices (ThreatPost)
- 2019/6/4 Newly discovered Tap ‘n Ghost attack can be used to target Android devices (CYWARE)
- 2019/6/5 Tap ‘N Ghost Attack – To Target Touchscreen Devices (HackersOnlineClub)
- 2019/6/5 Newly Discovered Tap ’n Ghost Attack Let Hackers to Remotely Control Android Smartphone (GBHackers)
- 2019/6/5 Tap ‘n Ghost Attack discovered by Security Researchers at Waseda University, Tokyo (TechnoidHub)
- 2019/6/7 TAP ‘N GHOST: A NOVEL ATTACK AGAINST SMARTPHONE TOUCHSCREENS (HACKADAY)